
Phishing is one of the oldest types of cyberattacks, dating back to the 1990s. Despite having been around for decades, it is still one of the most widespread and damaging cyberattacks.
As phishing messages and techniques become increasingly sophisticated, despite growing awareness and safety measures taken, many organisations and individuals alike are still falling prey to this pervasive scam. Below are the 12 common phishing types that you should know:
Spear phishing

Phishing attempts directed at specific individuals or companies are known as spear phishing. In contrast to bulk phishing, spear phishing attackers often gather and use personal information about their target to increase their probability of success. To be more specific, the subjects, contents, and titles of these phishing emails are dedicatedly designed to match well with the targets’ current jobs, hot social events, or personal affairs, etc., to reduce the targets’ safety precaution. Although often intended to steal data for malicious purposes, cybercriminals may also intend to install malware on a targeted user’s computer.
Angler Phishing
Angler phishing is the practice of masquerading as a customer service account on social media, hoping to reach a disgruntled consumer. Cybercriminals create illegal brand accounts/portals, first attract users’ attention (lantern attraction), and after building trust, they deliver actual phishing links to the followers of their accounts in social media such as Twitter, Facebook, Instagram, etc. This method is common in banks, e-commerce, retail, and other industries. It should be noted that, in addition to counterfeiting companies, counterfeiting corporate managers, and social celebrities are equally effective.
Business Email Compromise
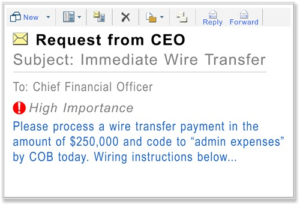
Business Email Compromise (BEC) is a type of scam targeting companies who conduct wire transfers and have suppliers abroad. Cybercriminals use social engineering skills to conduct counterfeiting and illegal activities by registering domain names similar to the clients’ names and sending relevant emails. Different from pure email spoofing (Email Spoofing, forged email headers, spreading phishing URL links, or malicious attachments), this type of phishing emails is often more subtle. The phishing target is generally the administrative departments and other financial departments. Since BEC aims at the administrator level, it brings greater harm to the enterprise, which also known as CEO Fraud.
Clone Phishing
Clone phishing is a type of phishing attack whereby a legitimate, and previously delivered, email containing an attachment or link has had its content and recipient address(es) taken and used to create an almost identical or cloned email.
Domain Spoofing
Domain spoofing, a common form of phishing, occurs when an attacker appears to use a company’s domain to impersonate a company or one of its employees. The goal of domain spoofing is to trick a user into interacting with a malicious email or a phishing website as if it were legitimate.
Evil Twin
An evil twin attack is a type Wi-Fi attack that works by taking advantage of the fact that most computers and phones will only see the “name” or ESSID of a wireless network. This actually makes it very hard to distinguish between networks with the same name and same kind of encryption.
When users connects to the ‘twin-wifi’, the attacker can steal their account names, passwords, and view the content of any attachments the user accesses after connecting to the malicious hotspot. This type of attack is also known as a Starbucks scam, because it often takes place in coffee shops.
Smishing

A form of phishing, smishing is when someone tries to trick you into giving them your private information via a text or SMS message.
The cybercriminals send text messages that appear to be from a legal source but actually contain malicious URLs to trick users into clicking and downloading malicious attachments. The text messages may contain discount coupons, prize information, free tickets, etc. Smishing is becoming an emerging and growing threat in the world of online security.
Vishing
Vishing (voice phishing) is a type of phishing attack that is conducted by phone and often targets users of Voice over IP (VoIP) services like Skype. Cybercriminals also use mobile applications and other technologies to tamper with or even completely hide the caller number. In most cases, they pretend to be bank staff or managers in relevant departments and declare that the user has violated the law, or the credit card needs to be closed immediately because of suspicious activities. Therefore, they need to ‘verify’ the user’s personal information before they can close the card and reissue a new card, developing circumstances that allow fraud to occur.
Watering Hole Phishing
The term ‘watering hole attack’ refers to predators in nature that lurk near watering holes in the hope of attacking a prey nearby. In the cyber world, these predators stay on the prowl near websites which are frequently visited by their prey. They wait for an opportunity to infect these websites with malware to make their target vulnerable. As this kind of phishing attack relies on a website trusted by the target group, the attack success rate is very high, even those groups that have rich experience in defending against spear attacks or other forms of phishing attacks could be caught.
Whaling

A whaling attack is essentially a spear-phishing attack but the targets are bigger – hence whale phishing. Where spear-phishing attacks may target any individual, whaling attacks are more specific in what type of person they target: focusing on one specific high level executive or influencer vs a broader group of potential victims.
Whaling relies on social engineering, and attackers usually know their targets well. They firstly collect target-related information from the Internet and various social media platforms, and then design specific phishing. Due to their highly targeted nature, whaling attacks are often more difficult to detect than standard phishing attacks.
Snowshoeing
Snowshoe spamming, also know as snowshoeing, is a sending technique that evolved in an attempt to avoid email filters. Generally, attackers push out messages via multiple domains and IP addresses. Snowshoe spammers spread their message over many different IP addresses, each used in low volume, to send the message. By doing this, reputation- or volume-based spam filtering technologies can’t recognize and block malicious messages right away. As a result, some of the messages make it to the email inboxes before the filters learn to block them. Hailstorm campaigns work the same as snowshoe, except the messages are sent out over an extremely short time span.
Pharming
Pharming is a cyberattack intended to redirect a website’s traffic to another, fake site. Pharming can be conducted either by changing the hosts file on a victim’s computer or by the exploitation of a vulnerability in DNS server software. Compromised DNS servers are sometimes referred to as ‘poisoned’. Pharming is a two-step process. At first, cybercriminals install malicious code on your computer or server. Then, the code sends you to a bogus website, where you may be tricked in providing personal information.
